
Gestione del debito e previsione del rischio finanziario
Combinando la nostra esperienza finanziaria e tecnologie all'avanguardia, Finance Active ti consente di gestire meglio i tuoi debiti e i rischi finanziari.
Finance Active è un fornitore leader di soluzioni per la gestione del debito e la previsione dei rischi finanziari, servire le esigenze di tesoreria e di investimento del settore pubblico locale, delle imprese e delle istituzioni finanziarie.
€1,7T
debito monitorato
2,500+
Clienti del settore pubblico
450+
Cliente del settore privato
4,000+
Clienti delle istituzioni finanziarie
Soluzioni
Tecnologie innovative del debito e del rischio finanziario

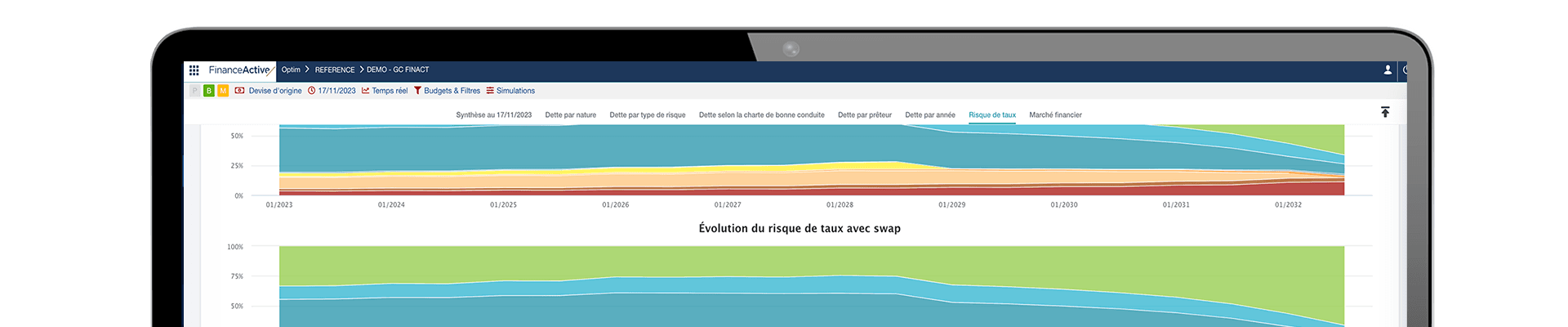
Optim Debt è una potente soluzione per la gestione del debito e degli investimenti che consente alle autorità pubbliche e locali di ottimizzare la gestione del debito e ridurre i rischi finanziari.

Optim Prospective è una soluzione di gestione delle previsioni finanziarie che consente alle autorità locali di creare scenari per ottimizzare la loro traiettoria finanziaria.

Riskedge è il nostro servizio di ingegneria finanziaria che consente agli enti del settore pubblico locale di accedere al supporto di esperti per missioni di alto valore.

Optim Grants & Subsidies è la nostra soluzione per massimizzare e salvaguardare le tue richieste di finanziamento pubblico e privato.

Fairways Debt è una soluzione leader di gestione del portafoglio debiti che ti consente di monitorare il tuo debito, ottimizzare i costi finanziari e ridurre l'esposizione al rischio.

Riskedge è il nostro servizio di ingegneria finanziaria che consente ai dipartimenti finanziari del settore privato di accedere al supporto di esperti per missioni di alto valore.






